-
.Net
-
Backup
-
Data Storage Containers
-
Docker Containers
-
Environment Management
- Swap-Domains
- Clone Environment
- Create Environment
- Environment Aliases
- Environment Aliases
- Environment Migration between Regions
- Environment Regions
- Environment Transferring
- Environment Variable
- Environment Variables
- Environment Variables(Apache meaven, Memcached)
- Environment Variables(Go)
- Environment Variables(JAVA)
- Environment Variables(Load Balancer)
- Environment Variables(Node.js)
- Environment Variables(PHP)
- Environment Variables(Ruby)
- How to Migrate a WordPress Site to BitssCloud PaaS
- How to migrate my environments from another Jelastic provider?
- HTTP Headers
- Java VCS Deployment with Maven
- Setting Up Environment
- Share Environment
- Why is my environment in sleeping mode?
- Show all articles (9) Collapse Articles
-
Java
- Environment Variables - Java custom Environment Variables
- Java App server Configuration
- Java Options and Arguments
- Multiple Domains on Tomcat server
- Secure Java Encryption and Decryption
- Spring Boot Standalone and Clustered Java Applications with BitssCloud
- Timezone Data for Java/PHP App Server
- Tomcat HTTP to HTTPS redirect
- WildFly server
-
LiteSpeed Web Server
-
OOM Killer
-
Python
-
Reseller SetUp
-
Secure Socket Layer (SSL)
-
Troubleshooting
-
Account Management
-
CDN
-
Databases
- Database Configuration
- Database Connection Strings
- Database Hosting in BitssCloud
- Environment Variables(Database)
- Galera Cluster not working
- How to export/Import Database via Command line
- How to install MSSQL server on Linux (2017)
- MariaDB/MySQL Auto-Сlustering
- MongoDB Database Backups
- PostgreSQL Database Backups
- PostgreSQL Database Replication
- PostgreSQL Master-Slave Cluster
- Remote Access to PostgreSQL
- Schedule Backups for MySQL and MariaDB Databases
- Scheduling Databases Backups
-
Domain Name Management
- Container Redeploy
- Custom Domain Name
- DNS Hostnames for Direct Connection to Containers
- How to Bind Custom Domain via A Record
- How to Bind Custom Domain via CNAME
- Multiple Custom Domains on an Nginx Web Server
- Multiple Domains with Public IP
- Multiple Public IP Addresses for a Single Container
- Setup WordPress Multisite Network with Domain Mapping and CDN
-
Jenkins
-
Load Balancing
-
PHP
- Creating Environment for PHP
- Deploy PHP Project Via GIT SVN
- How to Check Change PHP Version in BitssCloud
- How to create environment for AngularJs/ReactJs
- How to Enable PHP Extensions
- How to Install Custom PHP Application
- Ion cube Loader
- MariaDB PHP connection
- MySQL PHP Connection
- NGINX PHP
- PHP App Server Configuration
- PHP Connection to MongoDB
- PHP security settings
- PHP Session Clustering
- PostgreSQL PHP Connection
- Running Multiple Domain Names on Apache Server
- Security configuration for Apache
- Zero Downtime (ZDT) Deployment for PHP
- Show all articles (3) Collapse Articles
-
Release Notes
-
Ruby
-
SSH
-
Wordpress
-
Application Management
-
Cluster
-
Deploying Projects
-
Elastic VPS
- CentOS VPS
- Elastic VPS configuratation
- Elastic VPS with full root access
- Installation of cPanel in BitssCloud
- Java Console Application with CentOS VPS
- Linux VPS Access via Public IP
- Linux VPS Access via SSH Gate
- Setting Mail Server Inside CentOS VPS
- Setting Mail Server Inside CentOS VPS
- SSH Access to VPS Gate
- Ubuntu VPS
- Ubuntu with CSF Firewall
-
High Availability
-
Jitsi
-
Node.js
-
Pricing System
-
Request Handling
-
Scaling
- Application Server with horizontal scaling
- Automatic Horizontal Scaling
- Automatic Horizontal Scaling: Multi Nodes
- Automatic Vertical Scaling
- Database Horizontal Scaling
- Docker Containers Horizontal Scaling
- Horizontal Scaling
- Load Balancer with horizontal scaling
- Memcached horizontal scaling
- Storage Container
- VPS Horizontal Scaling
-
Traffic Distributor
-
General
- Apache & NGINX Modules
- BitssCloud Dashboard Guide
- Build and Deploy Hooks
- Cron Job scheduler
- FFMPEG Setup
- File Synchronization
- FTP Overview
- FTP/FTPS Support in BitssCloud
- How to Deploy Magento into BitssCloud PHP Cloud
- How to Enable Expert Mode in JCA
- How to open a support ticket to BitssCloud
- Installation of FTP
- Kubernetes Cluster
- MarketPlace
- Reduce Cloud Waste with Automatically Scheduled Hibernation
- Run Configuration
- SFTP Protocols for Accessing BitssCloud Containers.
- Supported OS Distributions for Docker Containers
- Timezone Addon
- Two-Factor Authentication
- Types of Accounts
- Varnish
- Websockets Support
- What is Cloudlet
- What is PaaS & CaaS
- WordPress AddOn
- Zero Code Change Deploy with No Vendor Lock-In for Smooth Migration across Cloud Platforms
- Show all articles (12) Collapse Articles
-
Go lang
-
Wordpress category
-
Data Storage Container
-
Memcached
-
Account & Pricing
Ports
The fourth tab (Ports) provides you with the general information on managing Docker container’s ports at CloudJiffy:
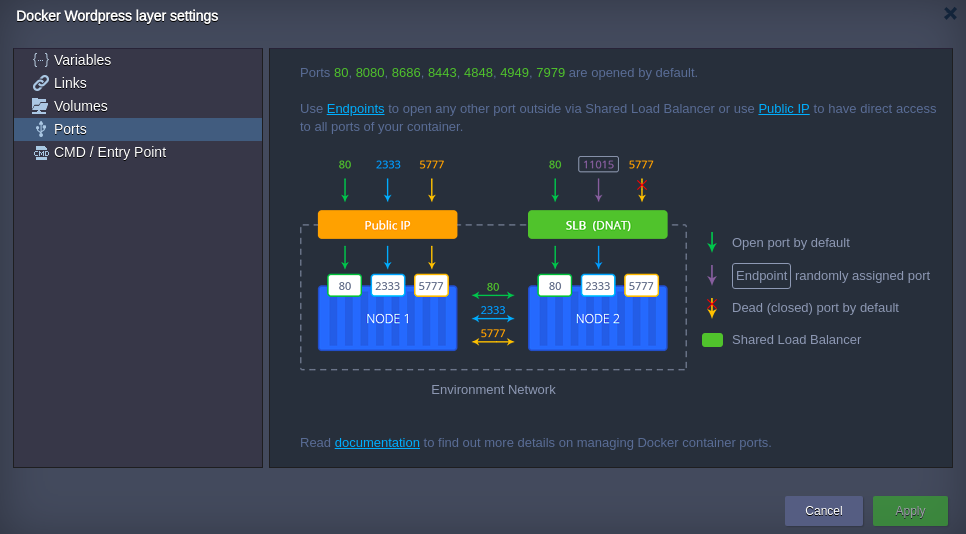
The following ports are opened by default:
- 80, 8080, 8686 – proxies HTTP traffic to HTTP (80 port)
- 4848, 8443, 4901–4910 – proxies SSL (HTTPS) traffic is proxied to SSL
- 443 – proxies SSL traffic is proxied to HTTP (80 port)
- 4949, 7979 – proxies SSL traffic to HTTP
Tip: Use the table below as a reference:
Additional ports can be opened using:
- Endpoints- maps the container internal port to random external via CloudJiffy Shared LB
- Public IP- provides a direct access to all ports of your container

Depending on the way chosen, just bind your service (application listener) to the received internal or external address.
Ports Auto-Redirect
CloudJiffy PaaS automatically redirects incoming requests to the application hosted within a container.
This process is performed on each container launch, so the corresponding application becomes available over the embedded Shared Load Balancer just after being deployed, without any manual intervention required.
According to it, you can bind the necessary port directly to the IP address (regardless of whether it is internal or external) your container was provisioned with. Pay attention that there is no need to expose ports in CloudJiffy because it uses PCS container-based virtualization, which is more technologically advanced compared with the native Docker containers’ implementation: it has the built-in support of the natural virtual host-routed network adapters.
So, if you’d like the required port to be accessible from the outside, you can either map via endpoint at CloudJiffy Shared LB (for being reachable over the automatically generated URL) or attach the external IP address to the appropriate container. After that, depending on the way chosen, just bind your service (app listener) to the received internal or external address.
Note that starting with CloudJiffy 4.0 version, the platform automatically detects the ports, that is listened to by the application on the TCP level, during image deployment. Then it separates the ones, that are commonly used by standard services (e.g. SSH, mail, databases, etc) and adds the required redirect to the iptables rules list (forwarding all the requests to the remained port, or the first one within the list). Such an operation is performed on each container’s launch, so that the corresponding application becomes available over the embedded Shared Load-Balancer just after being deployed, without any manual interventions required. However, in case you need to disable this functionality (e.g. for the app’s admin panel to be inaccessible from the outside), from CloudJiffy 4.6 you are able to set up the required auto-redirect settings manually right during the Docker container creation. For that, switch to the Variables configuration section and add the dedicated JELASTIC_EXPOSE parameter with the following values as possible:
- 0 or DISABLED or FALSE – to disable auto-redirect
- a number within the 1-65535 range – to define the required port for setting the corresponding redirect
- if any other value is stated, the auto-redirect functionality will work as usual
